IMDGuard: Protect Implantable Medical Devices
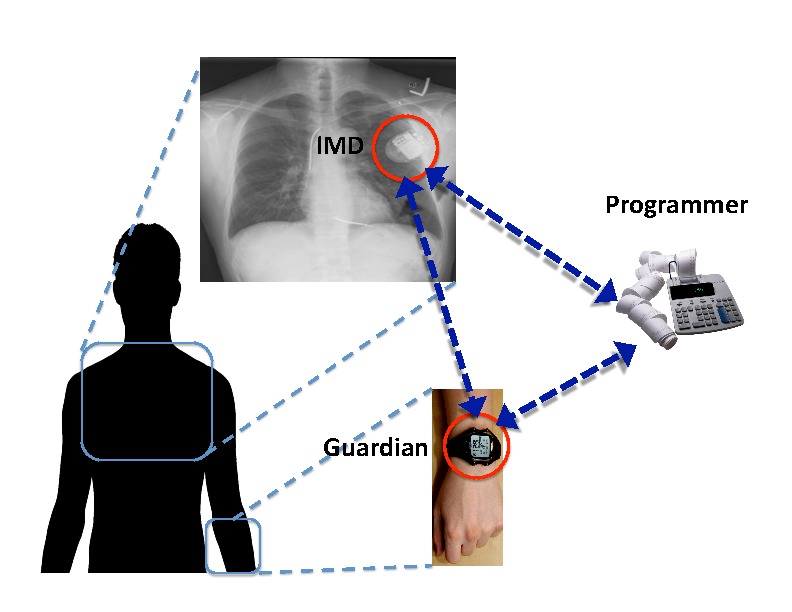
Qun LiRecent studies have revealed security vulnerabilities in implantable medical devices (IMDs). Security design for IMDs is challenging due to the requirement that IMDs remain operable in an emergency when appropriate security credentials may be unavailable. We designed and evaluated IMDGuard, a secure scheme for heart-related IMDs to fulfill this requirement. IMDGuard incorporates two novel techniques to provide appropriate protection for IMDs. One is an ECG based secure key establishment without prior shared secrets, and the other is an access control mechanism resilient to adversary spoofing attacks.
Project Homepage