Revisiting Android Reuse Studies in the Context of Code Obfuscation and Library Usages - MSR 2014 Online Appendix
This web page is a companion to our MSR 2014 paper entitled "Revisiting Android Reuse Studies in the Context of Code Obfuscation and Library Usages".
1. Data
Android apps
- The list of apps used in our study is available as a CSV file
- The list of apps used for the validation of the heuristic for classifying obfuscated/non-obfuscated apps is here
- The whole set apps and the classification provided by the heuristic is here
2. Data extraction
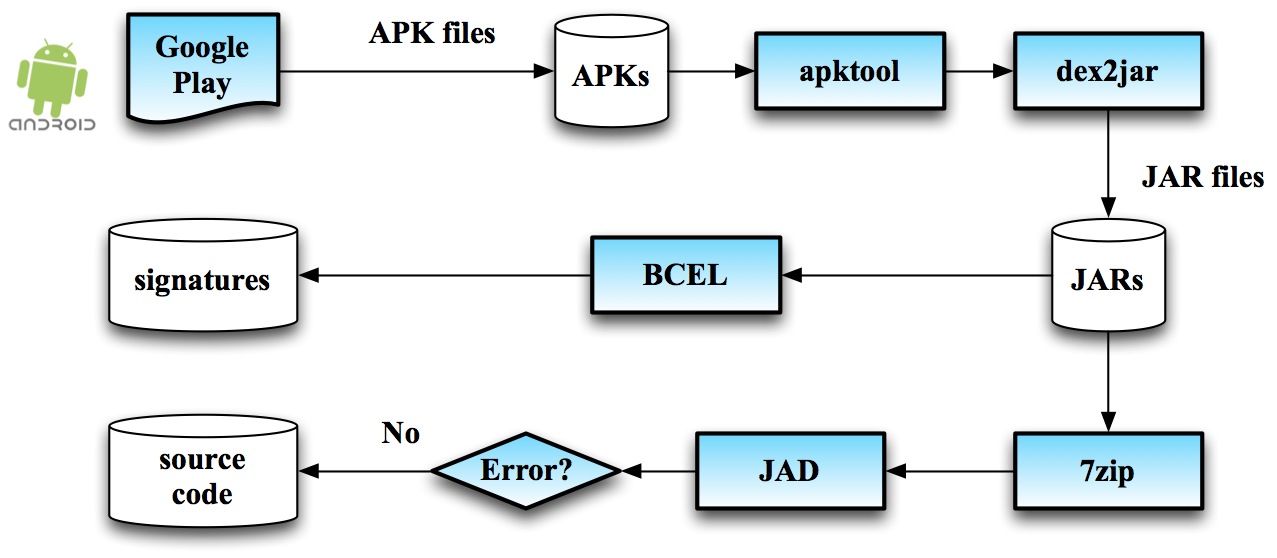
3. Results
RQ1-Does third party libraries impact the measurement of class cloning?
- Number of cloned signatures, files, and Percentage of Class Signatures Reused (PCSR) in our dataset including TPL (+TPL), and excluding TPL (-TPL)
RQ2-Does obfuscated code impact the measurement of class cloning?
- Number of cloned signatures, files, and Percentage of Class Signatures Reused (PCSR) in non obfuscated apps with TPL (-OBF), and non obfuscated apps excluding TPL (-(TPL,OBF)),
4. Tools
- Apache Commons BCEL library: required for extracting class signatures from JAR files.
- Apktool: required for extracting the contents of an APK file
- Dex2jar: used for getting JAR files from APK files
- JAD Java decompiler: for getting source code from JAR files
*Authors
- Mario Linares-Vásquez
- The College of William and Mary, VA, USA.
E-mail: mlinarev at cs dot wm dot edu - Andrew Holtzhauer
- The College of William and Mary, VA, USA.
E-mail: asholtzh at wm dot edu - Carlos Bernal-Cárdenas - Universidad Nacional de Colombia, Bogotá, Colombia
Email: cebernalc at unal dot edu dot co - Denys Poshyvanyk
- The College of William and Mary.
E-mail: denys at cs dot wm dot edu
